Security is vital in any organization as it aggregates alerts if malpractice exists in the working environment. It comes with best practices or protocols necessary for the organization to run the entire infrastructure smoothly.
AWS offers one such service w.r.t security named Security Hub. Once enabled, Security Hub will continuously scan the AWS accounts for configuration errors using various security standards and roll up security check results at the account and multi-account level to understand your overall security state.
It also uses summary dashboards and filtering rules to identify and prioritize which findings from AWS security services and partner security integrations are most important and require the most immediate attention.
What is R-SECURE?
R-SECURE is a solution built by Rapyder based on Security Hub AFSBP Standard (AWS Foundational Security Best Practices). This solution focuses on AFSBP control ids given by AWS for findings in the security hub console. It is developed so that it is possible to remediate almost all the findings with a single click. Using the R-SECURE solution, it is also possible to perform cross-account remediations.
Working Architecture
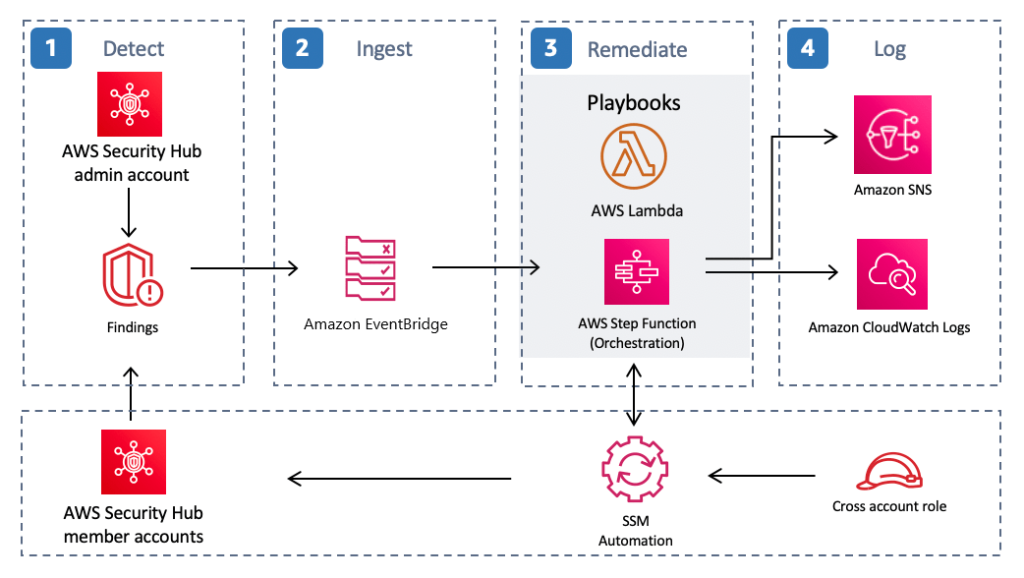
The above diagram illustrates the working of the R-SECURE Solution.
Steps to Remediate
Let’s take an example of control ID EC2.19, which checks whether unrestricted incoming traffic for the security groups is accessible to the specified ports like 80, 443, 3389, etc., that have the highest risk. It deletes the specified ports with Inbound Traffic source points as 0.0.0.0/0(Anywhere).
Note: Create a Security Group with ports 80 and 443 with the Inbound Traffic source points as 0.0.0.0/0 and one port as 3389 with the Inbound Traffic source point (MyIP) as given in the image below for this example.
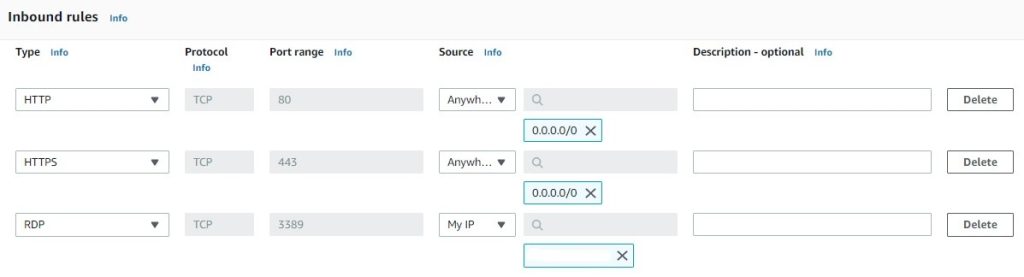
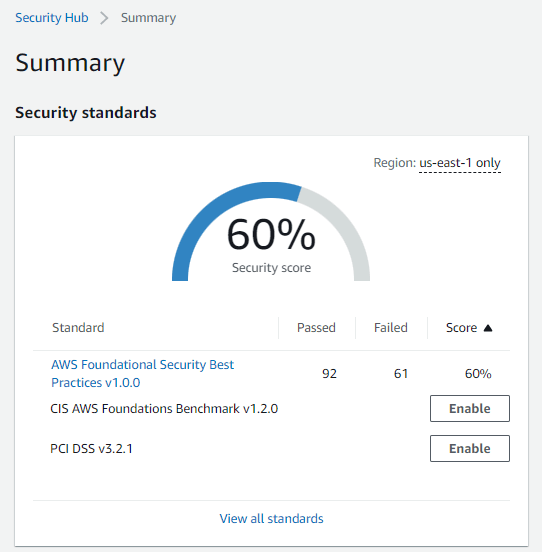
1. Open Security Hub from AWS Console, click on Go to Security Hub and select the Security Standard AFSBP (AWS Foundational Security Best Practices).
Note: The Security Group with the mentioned configuration created initially will now show up in the Security Hub Findings.
2. In AFSBP Security standards, type EC2.19 in the filter windows to see the finding.
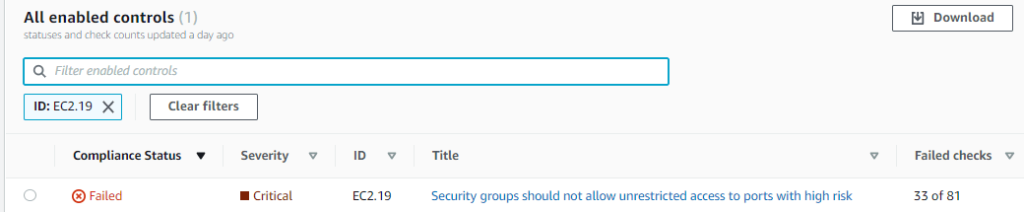
3. Confirm the finding from the resource attribute and make sure the compliance status of EC2.19 is Failed to remediate.
4. Open the EC2.19 finding.
5. Select the finding, and from Actions, click on R-SECURE Remediate.
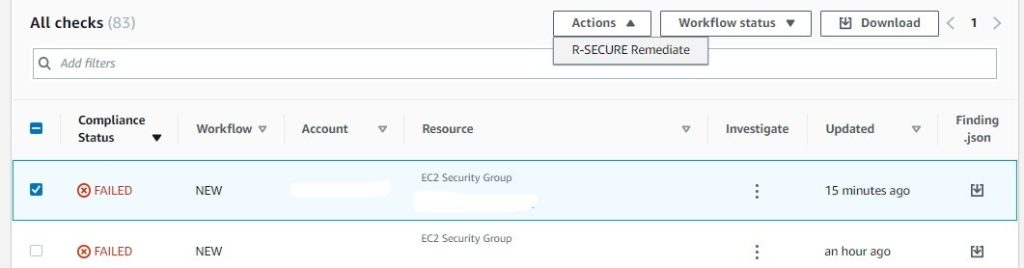
6. Once clicked, the EC2.19 finding will remediate.
7. To see the entire workflow of EC2.19, open Step functions from AWS Console.
8. Click on burger-shaped three dashes on the left of the screen, and select State Machines from the list
9. From the State Machine list, select R-SECURE-Orchestrator.
10. In R-SECURE-Orchestrator, select the execution with the status Running.
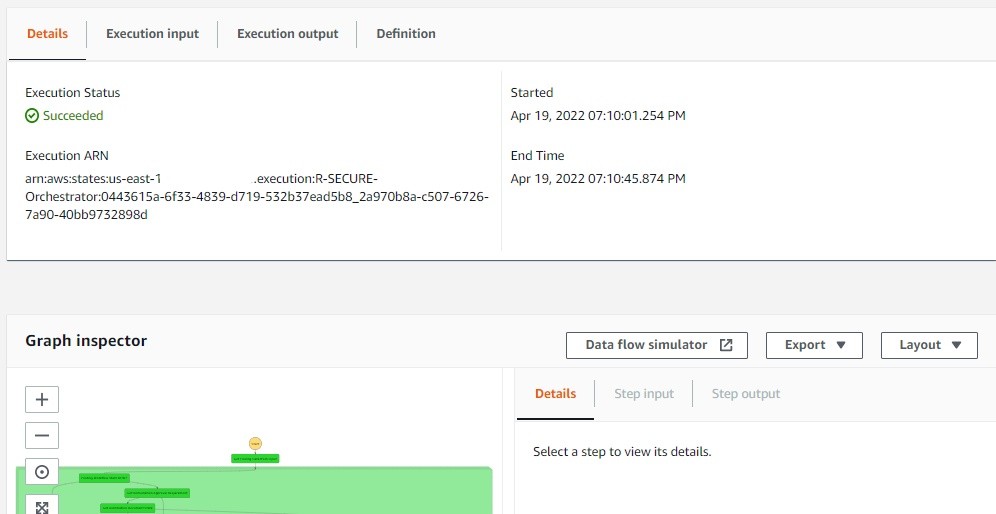
11. Once execution with status running is opened, the entire workflow of EC2.19 can be seen in Graph Inspector. The Execution status changes from Running to Succeeded once the entire workflow has succeeded.
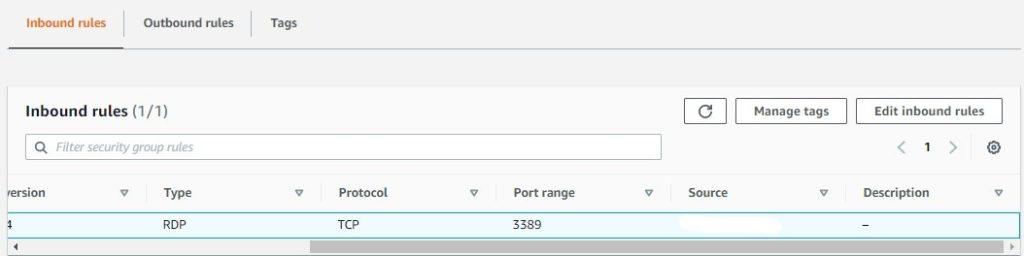
12. Once the status is Succeeded, the ports (80, 443) configured initially with source points 0.0.0/0 are deleted from the list. The image below confirms that port 3389 with the source point set as (MyIP) has not been deleted.
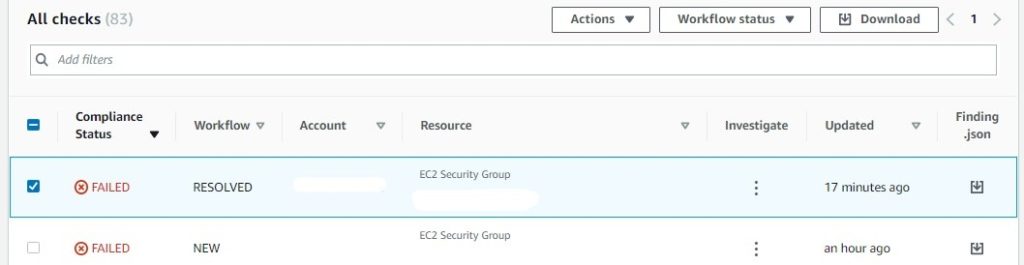
13. Lastly, to confirm, go to Security Hub, where the workflow status of EC2.19 has been changed from NEW to RESOLVED as the remediation is complete.
Conclusion
As stated earlier, Security plays a vital role in a working environment, and the R-SECURE solution using Security Hub as its core helps to follow the best practices and works to remediate finding according to the AWS security standards and compliance. It shows all the control with the Severity level, Compliance status, and the number of Failed Checks and helps to remediate almost all findings with a single click. To know more about R-SECURE, Contact us.
To know more about such services, see the Blogs.
Happy Reading 😊
Written by – Chaitanya Karadkhedkar







